Multi-factor authentication (MFA) in Azure AD
Multi-factor authentication requires more than one form of verification, such as a trusted device or a fingerprint scan, to prove that an identity is legitimate. It means that, even when an identity’s password has been compromised, a hacker can't access a resource.
Multi-factor authentication dramatically improves the security of an identity, while still being simple for users. The extra authentication factor must be something that's difficult for an attacker to obtain or duplicate.
Azure Active Directory Multi-Factor Authentication works by requiring:
Something you know – typically a password or PIN and
Something you have – such as a trusted device that's not easily duplicated, like a phone or hardware key or
Something you are – biometrics like a fingerprint or face scan.
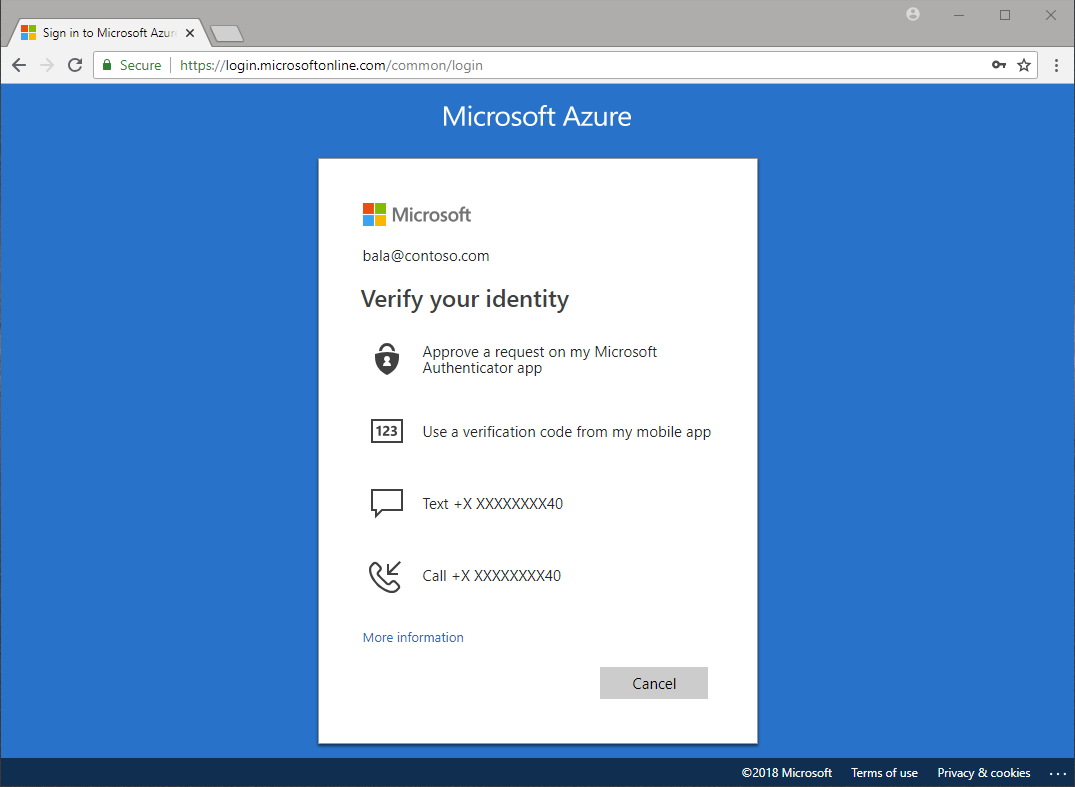
Multi-factor authentication verification prompts are configured to be part of the Azure AD sign-in event. Azure AD automatically requests and processes multi-factor authentication, without you making any changes to your applications or services. When a user signs in, they receive a multi-factor authentication prompt, and can choose from one of the additional verification forms that they've registered.
An administrator can require certain verification methods, or the user can access their MyAccount to edit or add verification methods.
The following additional forms of verification, described in the previous unit, can be used with Azure AD Multi-Factor Authentication:
Microsoft Authenticator app
Windows Hello for Business
FIDO2 security key
OATH hardware token (preview)
OATH software token
SMS
Voice call
Security defaults and multi-factor authentication
Security defaults are a set of basic identity security mechanisms recommended by Microsoft. When enabled, these recommendations will be automatically enforced in your organization. The goal is to ensure that all organizations have a basic level of security enabled at no extra cost. These defaults enable some of the most common security features and controls, including:
Enforcing Azure Active Directory Multi-Factor Authentication registration for all users.
Forcing administrators to use multi-factor authentication.
Requiring all users to complete multi-factor authentication when needed.
Security defaults are a great option for organizations that want to increase their security posture but don’t know where to start, or for organizations using the free tier of Azure AD licensing. Security defaults may not be appropriate for organizations with Azure AD premium licenses or more complex security requirements. To learn more, visit What are security defaults?
Last updated